Business software developers, secure applications vendors, and infosec specialists work as hard as possible to warn people about all possible threats that can impact the information privacy of business entrepreneurs, enterprises, small businesses and teams.
However, the number of cybercrimes is still present in big numbers. The variety of possible threats and ways of their distribution is impressive.
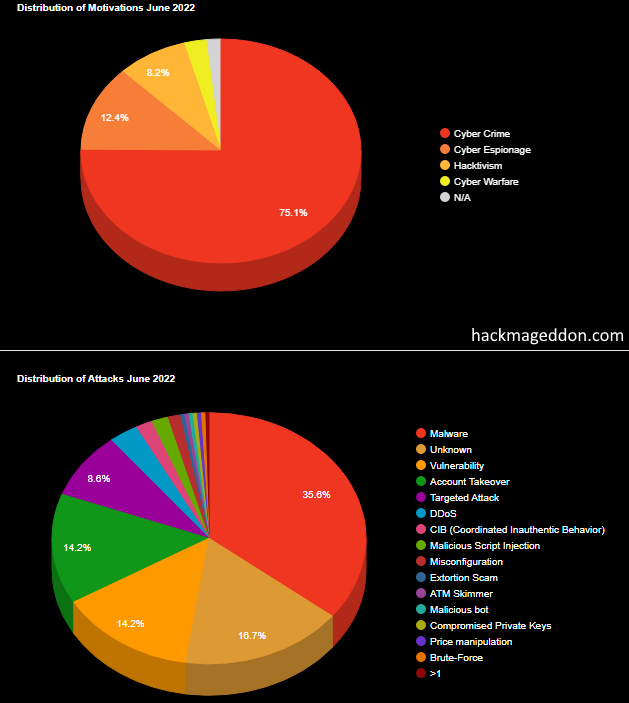
Let’s take a look at the image above and discuss some of the most popular ones. We see that malware is on the top of the list. Hackers are tricky. They always come up with new ideas on how to exploit a person’s device to get the information they need. For example, russian hackers used such cloud services as DropBox and Google Drive to distribute malicious software to the embassy in Portugal.
Another disgusting example also includes russian hackers: they created a page on behalf of Ukrainian defenders and placed a malicious app that allegedly help to fight against russian aggression.
Means of cyberattack distribution and their impact on information privacy
Malware is very dangerous — you may lose all the data as soon it launches on your computer.
How to avoid malware threats? Even if you trust cloud services, always check the sender of a link to these services. Remember about phishing — the hacker can mask himself as your teammate as send you an email allegedly from a corporate email.
Vulnerability. What does that mean? It means that the targeted system probably has poor security measures, public servers managed by an untrusted third party, or open-source code (hackers learned it and found the way to break through).
How to improve your information privacy? Use software that you can fully control.
You must be able to manage the server that processes all data; control user access by assigning certain rules and permissions; track all connections to the server, and remove suspicious ones. It is not impossible with WhatsApp, Viber, Telegram, Slack, etc.
Account takeover. That is only possible when using public services. Any information posted on the internet will never be private despite all the delusional statements from large service providers.
How to avoid being hacked? Again, switch to self-hosted software. Services based on public servers are always vulnerable and cannot provide decent privacy measures.
Or… at least keep your password strong and updated!