At the end of 2023, the state of healthcare security was catastrophic. It was reported that breaches increased by 93% from 2018 to 2022.
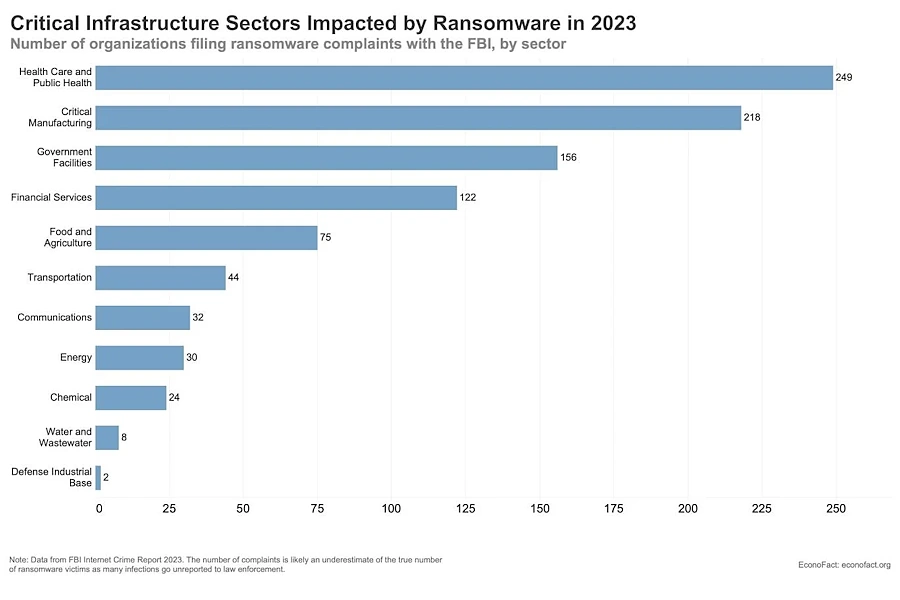
It turned out, that healthcare digital systems are very vulnerable as ransomware attacks are performed easily. Threat actors still use ransomware to demand redemption for leaked data, and hospitals are usually left with no choice but to pay the price with the hope of saving their patients’ data.
Needless to say, today’s attacks on the healthcare system have become more cruel because infected software means no access to a patient’s history which puts their treatment at risk.
Why healthcare security is #1 target for hackers?
Various systems from various vendors make the job easier. And if it has access to Wi-Fi and external internet, it automatically becomes publicly available for experienced hackers. For example, a patient with a pacemaker is a possible target because this device transfers data to a hospital via the Internet.
Healthcare stores huge amounts of data. It is not only the patient’s health history but also financial information, social security numbers, and other data that attackers can find valuable for further threats.
Empathy and responsibility. A person’s life is the number one priority. If the hospital fails at keeping the patient’s data secure, it must do anything to save their life. Attackers play with people’s empathy and compassion to reach their criminal goals.
How do we reduce the risks of ransomware attacks?
Investing in professional communication systems can help keep sensitive data away from public access.
Self-hosting is not an option anymore, it is a must.
Sorting or separating one data type from another and storing it on a private reliable server reduces the chances of unauthorized access.
Duplicated systems. In an aircraft, there are many duplicate operations in case of emergency. Airlines invest a lot in security because their work involves people’s lives.
The same is true with healthcare systems, one of the most critical infrastructures. More control management, more access monitoring, and checking — any amount of security measures is never enough.